How Network Monitoring Helps Ensure Compliance with Industry Regulations
In today’s hyper-connected digital landscape, organizations face increasing pressure to comply with industry regulations that govern data privacy, cybersecurity, and operational integrity.
From GDPR and HIPAA to PCI-DSS and
ISO standards, regulatory frameworks are becoming more stringent, and the
consequences of non-compliance—ranging from financial penalties to reputational
damage—are more severe than ever.
One of
the most effective ways to stay ahead of these requirements is through network
monitoring. Far beyond its traditional role of ensuring uptime and performance, network monitoring now plays a critical role in helping
organizations meet compliance mandates by offering visibility, control, and
accountability across IT infrastructure.
Understanding Compliance in the
Digital Age
Compliance
refers to an organization’s adherence to laws, regulations, guidelines, and
specifications relevant to its business processes. These can be
industry-specific (e.g., HIPAA for healthcare, PCI-DSS for finance) or
region-specific (e.g., GDPR in the EU, CCPA in California).
Key
compliance goals include:
- Data protection and privacy
- System integrity and
availability
- Auditability and
traceability
- Incident detection and
response
Meeting
these goals requires continuous oversight of network activity, which is where
network monitoring becomes indispensable.
What Is Network Monitoring?
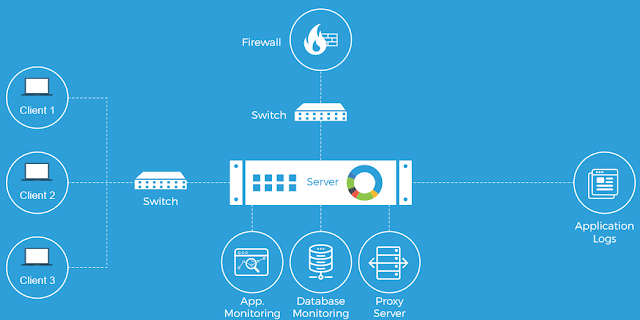
Network
monitoring involves the real-time tracking of network components—servers,
routers, switches, endpoints, and applications—to ensure optimal performance,
detect anomalies, and maintain security. It uses tools and protocols to
collect, analyze, and report on metrics such as:
- Bandwidth usage
- Latency and packet loss
- Device health and uptime
- Traffic patterns
- Unauthorized access attempts
- Configuration changes
Modern
network monitoring solutions also integrate with SIEM (Security Information and
Event Management) platforms, log management tools, and ITSM systems to provide
a unified view of network health and security.
How Network Monitoring Supports
Compliance
Let’s
break down the specific ways network monitoring helps organizations meet regulatory
requirements:
1. Real-Time Threat Detection and Response
Regulations
like GDPR and HIPAA require organizations to detect and respond to data
breaches promptly. Network monitoring tools can:
- Identify unusual traffic
patterns
- Detect unauthorized access
attempts
- Trigger alerts for
suspicious activity
- Integrate with incident
response workflows
This
proactive approach helps organizations contain threats before they escalate,
reducing the risk of non-compliance.
2. Audit Trails and Reporting
Most compliance
frameworks mandate detailed logs of system activity. Network monitoring tools
automatically generate:
- Event logs for access, changes, and
failures
- Configuration histories for devices and
applications
- User activity reports for accountability
These logs
serve as audit trails that can be presented during regulatory inspections or
internal reviews.
3. Data Integrity and Availability
Regulations
like ISO 27001 and SOC 2 emphasize the importance of maintaining data integrity
and system availability. Network monitoring ensures:
- Redundancy and failover
mechanisms are
working
- Performance bottlenecks are identified and resolved
- Critical systems remain accessible and
secure
This
helps organizations demonstrate that their infrastructure supports business continuity
and data reliability.
4. Configuration Compliance
Unauthorized
or undocumented changes to network configurations can lead to vulnerabilities.
Network monitoring tools track:
- Configuration drift across devices
- Unauthorized changes to firewall rules or access
controls
- Policy violations in network setups
By
maintaining configuration baselines, organizations can ensure their systems
remain compliant with internal and external standards.
5. Access Control and Identity Management
Regulatory
mandates often require strict access controls. Network monitoring supports:
- Role-based access tracking
- Authentication and
authorization logs
- Alerts for privilege
escalation or failed login attempts
This
ensures that only authorized personnel access sensitive systems, reducing the
risk of insider threats and data leaks.
Compliance Frameworks That Benefit from
Network Monitoring
Here’s
how network monitoring aligns with some major compliance standards:
|
Regulation |
Network Monitoring Contribution |
|
GDPR |
Detects
data breaches, logs access, supports incident response |
|
HIPAA |
Tracks
access to patient data, ensures system availability |
|
PCI-DSS |
Monitors
network traffic, detects unauthorized access |
|
ISO
27001 |
Supports
risk assessment, logs system changes |
|
SOX |
Provides
audit trails for financial systems |
|
NIST |
Enables
continuous monitoring and threat detection |
Features to Look for in a
Compliance-Ready Network Monitoring Tool
To
effectively support compliance, your network monitoring solution should offer:
- Real-time alerts and
dashboards
- Automated log collection and
retention
- Role-based access and user
tracking
- Integration with SIEM and
ITSM platforms
- Customizable reporting
templates
- Policy enforcement and
configuration tracking
These
features not only help meet compliance goals but also improve overall IT
governance.
Best Practices for Using Network
Monitoring for Compliance
To
maximize the compliance benefits of network monitoring, organizations should:
✅ 1. Define Compliance Objectives
Align
monitoring goals with specific regulatory requirements relevant to your
industry.
✅ 2. Centralize Monitoring
Use
unified platforms to monitor all network components from a single dashboard.
✅ 3. Automate Reporting
Schedule
regular compliance reports and ensure logs are retained for mandated periods.
✅ 4. Conduct Regular Audits
Review
monitoring data to identify gaps, misconfigurations, or policy violations.
✅ 5. Train Staff
Ensure IT
teams understand how to use monitoring tools to support compliance efforts.
The Business Value of Compliance
Through Monitoring
Beyond
avoiding fines and legal trouble, compliance-driven network monitoring offers:
- Improved security posture
- Operational efficiency
- Customer trust and brand
reputation
- Faster incident response
- Better resource allocation
In
essence, it transforms compliance from a checkbox exercise into a strategic
advantage.
Conclusion
In an era
where data breaches and regulatory scrutiny are on the rise, network monitoring
is no longer optional—it’s essential. By providing real-time visibility,
automated reporting, and proactive threat detection, network monitoring
empowers organizations to meet compliance requirements confidently and
efficiently.
Whether
you're a healthcare provider safeguarding patient records, a financial
institution protecting transactions, or a tech firm managing user data, network
monitoring is your frontline defense in the battle for compliance.



Comments
Post a Comment